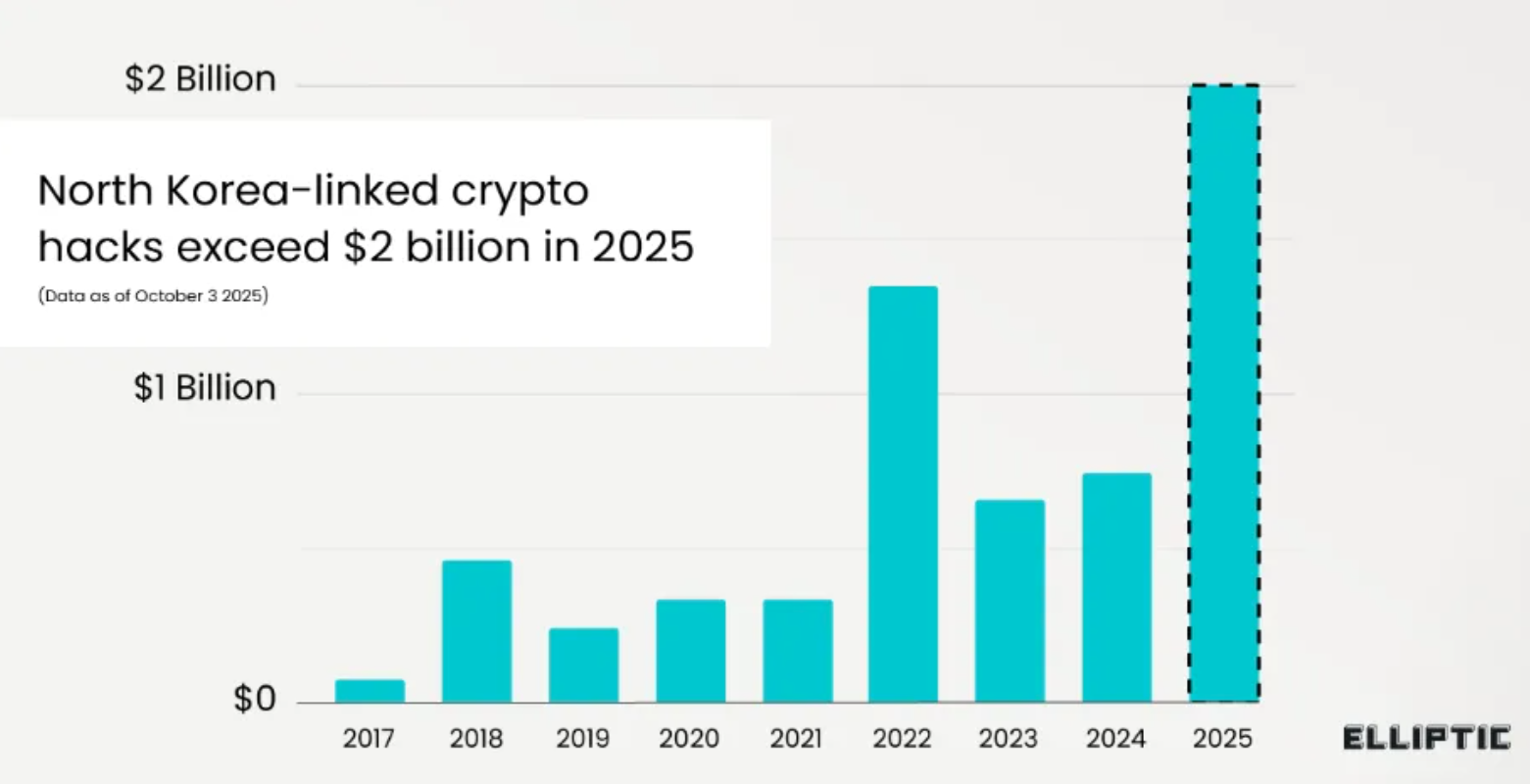
According to blockchain analytics firm Elliptic, groups linked to North Korea have stolen over $2 billion in digital assets since January 2025—nearly triple the tally for all of 2024. The cumulative, publicly known damage from DPRK cyber heists has now surpassed $6 billion. The year’s surge was driven by the historic breach of Bybit in February (roughly $1.46–1.5 billion), alongside incidents involving LND.fi, WOO X, and Seedify.
The Year at a Glance: Who, When, How Much
- Bybit (Feb 21–23, 2025) — the largest crypto hack on record, around $1.46–1.5 billion. The theft was widely attributed to DPRK-linked operators; the funds were rapidly fragmented and funneled through thousands of addresses.
- LND.fi (May 2025) — an issue in a modified Aave fork enabled the outflow of about $1.18 million.
- WOO X (July 24, 2025) — roughly $14 million lost via targeted phishing of specific accounts; indicators pointed to a known DPRK cluster.
- Seedify (Sept 23–25, 2025) — exploit of the SFUND bridge, about $1.2 million in losses; publicly discussed as likely tied to North Korean actors.
Industry snapshot for July: the crypto sector suffered 17 attacks totaling around $142 million, a notable jump from June.
Tactics Have Shifted: Fewer Code Exploits, More People
In 2025, DPRK actors increasingly prioritized social engineering over pure technical exploits. Playbooks include spear-phishing, malicious “trading apps,” fake recruiters, credential theft targeting employees and VIP clients, and compromise of work devices and private keys. These techniques align with long-running campaigns often tracked under umbrellas like TraderTraitor/AppleJeus.
Laundering at Scale: “Chain Through Chain”
Rather than relying on a single mixer, attackers route funds through multi-stage paths designed to blur provenance:
- Chain-hopping: rapid swaps and transfers across multiple blockchains and bridges.
- Cascaded mixing: splitting sums into shards and cycling them through sequential mixers and lesser-known networks.
- Refund-address pivots: exploiting return-address mechanics to “reset” trails into fresh wallets.
Elliptic and other analytics firms note that cross-chain obfuscation has become central since the Bybit theft.
Why the Regime Does It
International bodies and regulators have repeatedly documented how crypto thefts help finance North Korea’s WMD programs—from ballistic missiles to nuclear development. The 2025 spike underscores how a sanctioned state can operate as a cyber privateer, converting stolen digital assets into hard-to-trace funding streams.
Why It’s Getting Harder (Despite the Headlines)
Blockchains are paradoxical: they act like internet cash but also as public ledgers. The ecosystem is getting better at:
- Tagging wallets linked to known DPRK clusters,
- Freezing assets when they touch centralized ramps,
- Reconstructing multi-hop routes—even across obscure chains—and correlating them with known campaigns.
Elliptic’s latest work emphasizes that greater on-chain visibility has helped stall portions of cash-outs.
What It Means for Companies and Wealthy Individuals
Highest-risk profiles: centralized platforms and fintechs holding large hot-wallet balances; funds/VIPs with broad permissions; teams with distributed signing keys.
Practical minimum defense checklist:
- Zero-trust for people and software: dedicated devices for keys and trading tools; no sideloaded apps.
- Two-person controls with limits: “four-eyes” for large transfers; withdrawal and address-change time locks.
- Cold storage with migration policies: automatic key rotation; warm-wallet procedures; incident simulations.
- 24/7 on-chain monitoring: alerts for anomalous bridges/mixers/DEX aggregators; sanctions and risk-list integration.
- Anti-phishing hygiene: staff training; block file/link opens from messengers; operational accounts without signing rights.
- Rapid response plan: pre-arranged channels with analytics firms and exchanges to freeze funds fast; templated legal notices.
Context and Momentum
- Mid-July estimates already placed year-to-date thefts above $2.17 billion, putting 2025 on pace to rival or exceed prior records.
- Monthly intel roundups echoed the upswing: $142 million across 17 incidents in July alone.